14) which of the following are breach prevention best practices
Administrative actions and policies and procedures that are used to manage the selection development implementation and maintenance of security measures to protect electronic PHI. The following are high-level best practices for preventing breaches.

Adversaries Increasingly Target Cloud Environments Crowdstrike
Employees have an important role in keeping their organizations secure.
. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively. Implementing encryption standards and backup policies to decrease risks and make sure that software is up. Train Employees on Security Awareness.
Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. Identity theft resulting from using a. Which of the following are breach.
14 which of the following are breach prevention best practices. Perform suspicious email training exercises to help employees identify potentially nefarious emails. Two-factor authentication is a security feature that requires.
14 which of the following are breach prevention best practices. There are steps and practices that you can implement for breach prevention. Which of the following are breach prevention best practices.
In this type of data breach a. Set up two-factor authentication for every account. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022.
Require specific authorization and credentials to access sensitive information. Which of the following are breach prevention best practices. A breach as defined by the DoD is broader than a HIPAA breach or breach defined by HHS.
Invest in security automation. Which Of The Following Are Breach Prevention Best Practices. Fixing the problems that caused the breach to prevent its recurrence.
Vulnerability assessment is the process intended to identify classify and prioritize security threats and. Best Practices in Breach Prevention - Minimizing the Risk of a Breach. However before jumping to Breach Prevention Best Practices lets get to know frequently observed Data Breach types.
Which of the following are breach prevention best practices. It is better to acknowledge that data breaches are inevitable than to assume your organization is. Identity sensitive data collected stored.
Best Practices for Preventing a Data Breach. Data Breach by an Insider. Which of the following are breach prevention best practices.
Information technology and the associated policies and procedures that are used to protect and control access to ePHI intrusion. All of the above. Companies that leveraged artificial intelligence machine learning.
An incidental use or disclosure is. A breach as defined by the dod is broader than a hipaa breach or breach defined by hhs. A- Access only the minimum amount of PHIpersonally identifiable information PII necessary.

6 Most Common Causes Of Data Leaks In 2022 Upguard

Top 14 Data Security Best Practices
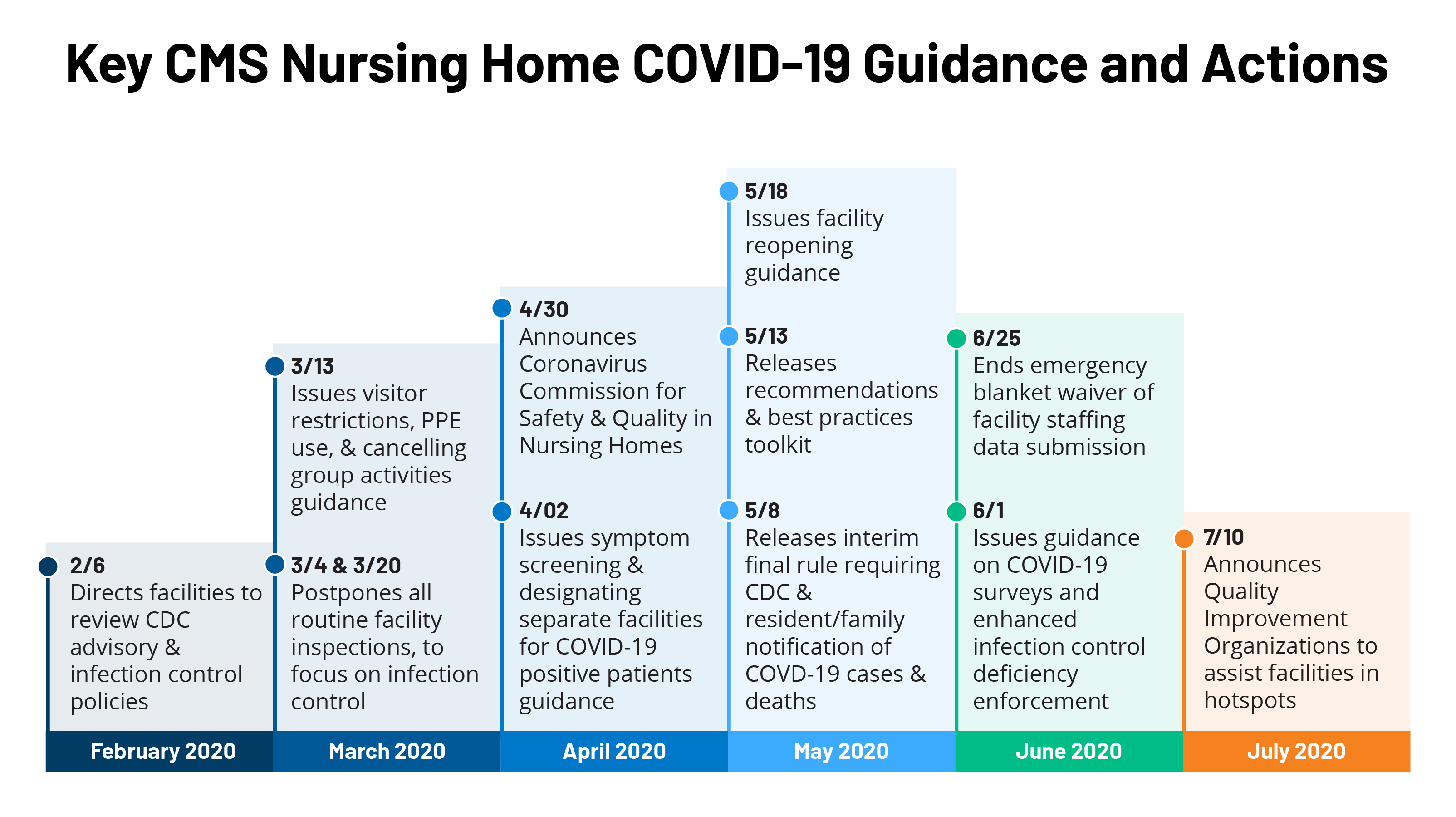
Key Questions About Nursing Home Regulation And Oversight In The Wake Of Covid 19 Kff
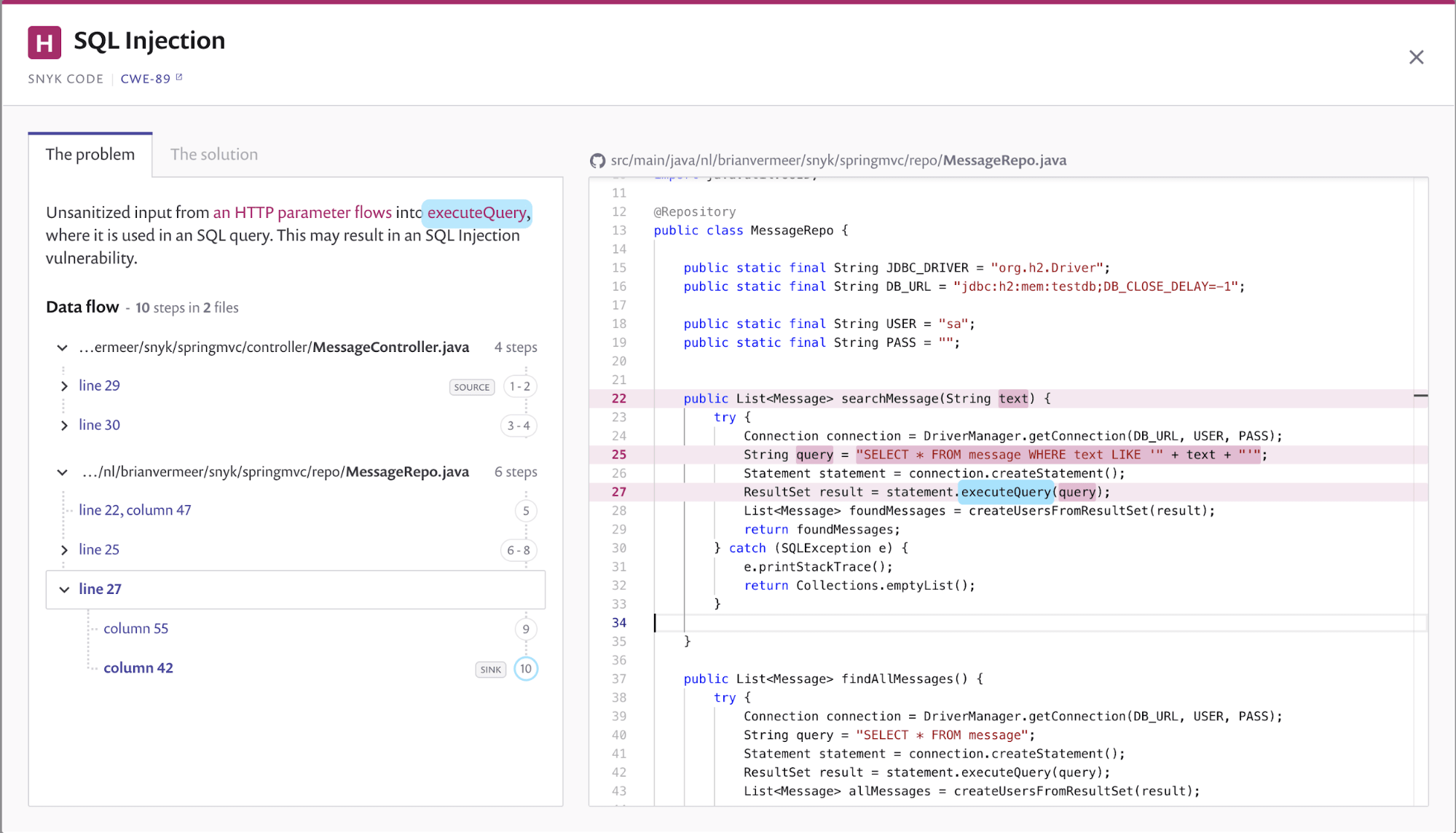
8 Best Practices To Prevent Sql Injection Attacks Globaldots

13 Ways To Prevent Data Breaches In Healthcare

Top 10 Zero Day Attack Prevention Best Practices 2022 Cybertalk

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library

14 Top Data Security Risks Every Business Should Address

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

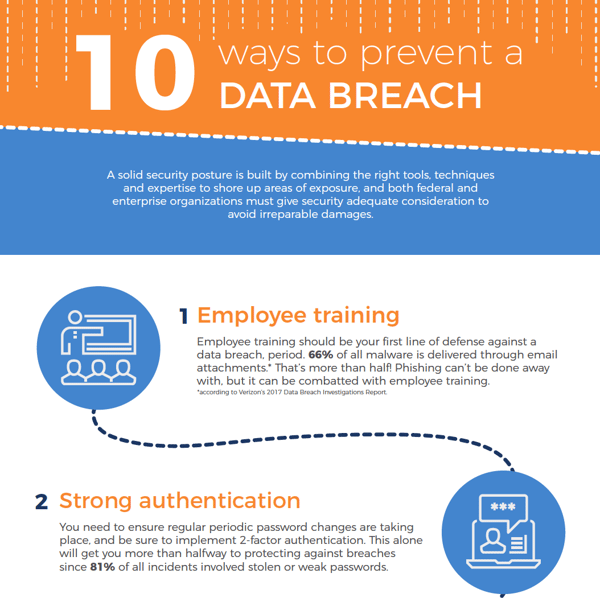
10 Ways To Prevent A Data Breach

Data Security Explained Challenges And Solutions

6 Most Common Causes Of Data Leaks In 2022 Upguard

Audit Log Review And Management Best Practices Strongdm

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

Preventing Data Breaches Starts With Creating And Training On Policies


